The Poodle Attack is a cryptographic vulnerability that targets the Secure Sockets Layer (SSL) and Transport Layer Security (TLS) protocols commonly used to secure communication on the internet. Unlike other attacks that focus on breaking the encryption itself, the Poodle Attack targets the SSL and TLS protocol implementations, exploiting a weakness in the design. This vulnerability allows an attacker to decrypt sensitive information, such as login credentials and session cookies, compromising the security of the communication.
The roots of the Poodle Attack can be traced back to the early days of SSL and the need for backward compatibility with older versions. The attack takes advantage of the SSLv3 protocol and its use of block ciphers with a padding scheme that can be manipulated by an attacker. As a result, even if a more secure protocol like TLS is being used, if the server supports SSLv3 as a fallback option, it can be exploited. To mitigate the risk, it is recommended to disable support for SSLv3 and use the newer TLS versions which are not vulnerable to the Poodle Attack.
A poodle attack is a cryptographic vulnerability that exploits the SSL 3.0 protocol. Attackers can intercept and decrypt the encrypted communication between a user’s browser and the server. This attack allows hackers to potentially access sensitive information such as login credentials or personal data. To prevent poodle attacks, it is recommended to disable support for SSL 3.0 and use more secure protocols like TLS 1.2 or higher.
The Dangers of the Poodle Attack
In the world of cybersecurity, there are numerous threats that can compromise the security and privacy of our online information. One such threat is the Poodle attack. This attack takes advantage of vulnerabilities in SSL version 3.0, an encryption protocol used to secure network connections. The Poodle attack can lead to the unauthorized access and manipulation of sensitive data, making it a serious concern for individuals and organizations alike. In this article, we will explore what the Poodle attack is, how it works, and what steps can be taken to prevent it.
Understanding the Poodle Attack
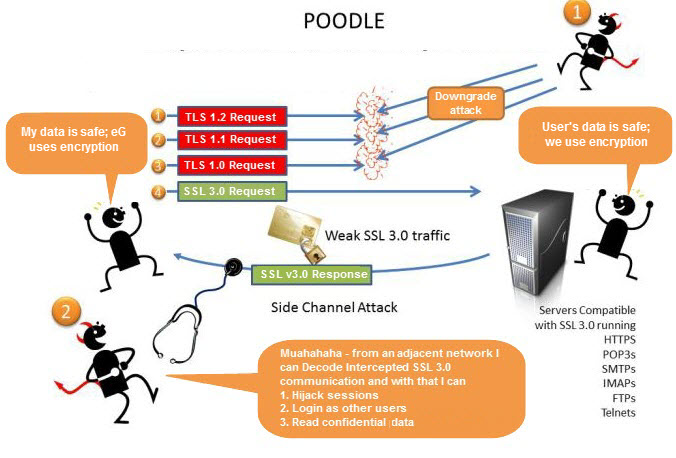
The Poodle attack, which stands for “Padding Oracle On Downgraded Legacy Encryption,” is a type of man-in-the-middle attack that targets the SSLv3 protocol. SSL, or Secure Sockets Layer, is a cryptographic protocol used to secure communication over the internet. SSLv3, the third version of SSL, was widely used until it was replaced by Transport Layer Security (TLS) due to security vulnerabilities.
The Poodle attack works by intercepting the communication between a client and a server and downgrading the connection from the more secure TLS to the vulnerable SSLv3. Once the connection is downgraded, the attacker can exploit a weakness in SSLv3 called the padding oracle attack. This attack allows the attacker to decrypt secure information, such as session cookies, and gain unauthorized access to the user’s account or sensitive data.
It’s important to note that modern browsers and websites no longer support SSLv3 due to its vulnerabilities. However, some older systems or misconfigured servers might still have SSLv3 enabled, making them susceptible to the Poodle attack.
How the Poodle Attack Works
Let’s take a closer look at the steps involved in a Poodle attack:
- The attacker intercepts the communication between a client and a server.
- The attacker forces the connection to downgrade from TLS to SSLv3.
- The attacker sends specially crafted requests to the server.
- The server’s response contains encrypted information.
- The attacker gradually decrypts the encrypted information by exploiting the padding oracle attack.
By decrypting the information, the attacker can gain access to sensitive data, such as login credentials, session cookies, or other confidential information exchanged between the client and the server.
Preventing the Poodle Attack
To protect against the Poodle attack, it is crucial to follow these preventive measures:
- Disable SSLv3: Ensure that SSLv3 is disabled on all servers and systems. This can prevent the downgrade from TLS to SSLv3, eliminating the vulnerability exploited by the Poodle attack.
- Update software and systems: Keep all software and systems up to date with the latest security patches. This includes web browsers, operating systems, and server software. Updates often include security fixes that address known vulnerabilities.
- Use secure encryption protocols: Implement and use the latest versions of encryption protocols, such as TLS 1.2 and TLS 1.3. These protocols have stronger security measures in place and are not vulnerable to the Poodle attack.
- Regular security audits: Conduct regular security audits to identify and address any weaknesses or vulnerabilities in your systems. This can help detect and prevent potential attacks, including the Poodle attack.
By following these preventive measures, individuals and organizations can significantly reduce the risk of falling victim to the Poodle attack and other similar vulnerabilities.
Conclusion
The Poodle attack is a serious threat that exploits vulnerabilities in SSLv3 to gain unauthorized access to sensitive data. By downgrading the connection from TLS to SSLv3, attackers can decrypt secure information and compromise the security and privacy of individuals and organizations. However, by disabling SSLv3, keeping software up to date, using secure encryption protocols, and conducting regular security audits, the risk of a Poodle attack can be significantly reduced. It is crucial for individuals and organizations to stay vigilant and take proactive steps to protect against this and other cybersecurity threats.
Key Takeaways: What is Poodle Attack?
- Poodle Attack is a security vulnerability that affects SSLv3, an outdated version of the SSL/TLS protocol.
- It allows attackers to exploit the weakness in SSLv3 to decrypt sensitive information like passwords and session cookies.
- To prevent this attack, it’s important to disable SSLv3 on servers and use more secure SSL/TLS versions.
- Web browsers have also updated their protocols to mitigate the risk of Poodle Attack.
- Regularly updating software and employing strong security measures can help protect against Poodle Attack.
Frequently Asked Questions
Poodle attack is a security vulnerability that affects the SSL 3.0 protocol, which is used for secure internet communications. It allows an attacker to exploit the protocol’s design flaw to decrypt sensitive information such as login credentials, personal data, or financial details.
1. How does a Poodle attack work?
A Poodle attack works by exploiting the design flaw in the SSL 3.0 protocol. The attacker tricks the target’s browser and server into using the SSL 3.0 protocol, even though more secure versions are available. They then decrypt the encrypted data transmitted between the browser and the server, gaining access to sensitive information.
This vulnerability is possible due to the protocol’s support for fallback to weaker encryption, such as the older SSL 3.0 version. The attacker exploits this weakness by making the browser and server fall back to SSL 3.0, enabling them to intercept and decrypt the data exchanged.
2. How can I protect myself from a Poodle attack?
To protect yourself from a Poodle attack, it is recommended to disable the use of the SSL 3.0 protocol on your web servers and in your web browsers. Most modern browsers and servers have already disabled SSL 3.0 by default. It is also crucial to keep your software and systems up to date with the latest security patches, as they often include fixes to vulnerabilities like Poodle.
Additionally, using more secure protocols such as Transport Layer Security (TLS) 1.2 or higher is strongly recommended. TLS 1.2 provides improved security and is not susceptible to the Poodle attack.
3. Can Poodle attack affect all websites and web browsers?
Poodle attack can affect websites and web browsers that still support the SSL 3.0 protocol. However, most modern browsers and servers have disabled SSL 3.0 by default, making them immune to this attack. Websites that have not updated their security configurations and still use SSL 3.0 are more susceptible to Poodle attacks.
It is essential for website administrators and developers to ensure that their web servers and websites are updated and use more secure protocols like TLS 1.2 or higher.
4. What are the potential consequences of a Poodle attack?
The potential consequences of a Poodle attack can be severe. As the attacker can decrypt sensitive information transmitted between the website and the user’s browser, it can lead to the exposure of confidential data such as login credentials, personal information, or financial details. This information can be used for identity theft, fraud, or other malicious activities.
Moreover, a successful Poodle attack can undermine the trust between users and websites, damaging a company’s reputation and potentially resulting in financial losses. It is essential for organizations to take necessary steps to prevent such attacks and protect the privacy and security of their users’ data.
5. Are there any known real-world instances of Poodle attacks?
Yes, there have been real-world instances of Poodle attacks. When the vulnerability was first discovered in 2014, it created a significant concern in the cybersecurity community. Many organizations promptly disabled SSL 3.0 on their servers and updated their security configurations.
While the prevalence of Poodle attacks has diminished over time due to improved security measures, it remains a relevant issue for websites and developers to address. Staying vigilant and proactive in implementing the necessary security measures is crucial to mitigate the risk of Poodle attacks.

SSLv3 Poodle Vulnerability | Password theft
A Poodle attack is a type of security vulnerability that allows an attacker to gain access to encrypted information. It takes advantage of a weakness in the Secure Sockets Layer (SSL) and Transport Layer Security (TLS) protocols, which are used to secure communication on the internet.
The attack works by downgrading the encryption protocol to an older, less secure version that is susceptible to attacks. This allows the attacker to intercept and decrypt sensitive information, such as login credentials or personal data. To protect against Poodle attacks, it is important to keep your software and systems up to date, and to disable support for vulnerable versions of SSL and TLS.
